How to Configure ‘FirewallD’ in RHEL/CentOS 7 and Fedora 21
Net-filter as we all know it’s a firewall in Linux. Firewalld is a dynamic daemon to manage firewall with support for networks zones. In earlier version, RHEL & CentOS 6 we have been using iptables as a daemon for packet filtering framework. In RHEL/CentOS 7 and Fedora 21 iptables interface is being replaced by firewalld.
It’s recommended to start using Firewalld instead of iptables as this may discontinue in future. However, iptables is still supported and can be installed with YUM command. We can’t keep Firewalld and iptables both in same system which may lead to conflict.
In iptables, we used to configure as INPUT, OUTPUT & FORWARD CHAINS but here in Firewalld, the concept which uses Zones. By default, there are different zones available in firewalld, which will be discussed in this article.
The basic zone which are like public zone and private zone. To make things work around with these zones, we need to add the interface with the specified zone support and then we can add the services to firewalld.
By default, there are many services are available, one of the best feature of firewalld is, it comes with pre-defined services and we can take these services as example to add our services by simply copying them.
Firewalld works great with IPv4, IPv6 and Ethernet bridges too. We can have the separate run-time and permanent configuration in firewalld. Let’s get started how to work with zones and create our own services and much more exciting usage of firewalld.
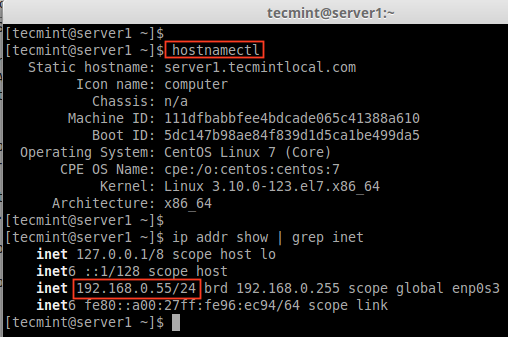
Our Testing Environment
Operating System : CentOS Linux release 7.0.1406 (Core) IP Address : 192.168.0.55 Host-name : server1.tecmintlocal.com
Step 1: Installing Firewalld Package
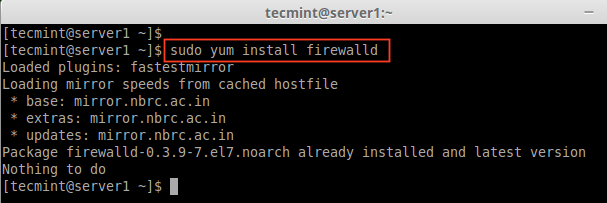
1. Firewalld package is installed by default in RHEL/CentOS 7 and Fedora 21. If not, you can install it using the following YUM command.
# yum install firewalld -y
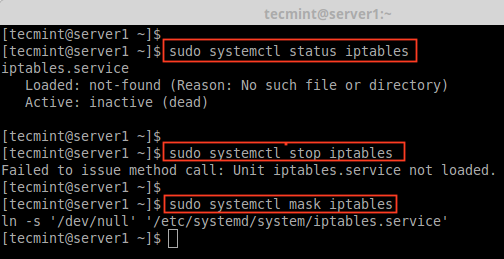
2. After firewalld package has been installed, it’s time to verify whether iptables service is running or not, if running, you need to stop and mask (not use anymore) the iptables service with below commands.
# systemctl status iptables # systemctl stop iptables # systemctl mask iptables
Stpe 2: Discussing Firewalld Components
3. Before heading up for firewalld configuration, I would like to discuss about each zones. By default there are some zones available. We need to assign the interface to the zone. A zone define that the zone was trusted or denied level to the interface to get connection. A zone can contain services & ports. Here, we’re going describe each zones available in Firewalld.
- Drop Zone: Any incoming packets are dropped, if we use this drop zone. This is same as we use to add iptables -j drop. If we use the drop rule, means there is no reply, only outgoing network connections will be available.
- Block Zone: Block zone will deny the incoming network connections are rejected with an icmp-host-prohibited. Only established connections within the server will be allowed.
- Public Zone: To accept the selected connections we can define rules in public zone. This will only allow the specific port to open in our server other connections will be dropped.
- External Zone: This zone will act as router options with masquerading is enabled other connections will be dropped and will not accept, only specified connection will be allowed.
- DMZ Zone: If we need to allow access to some of the services to public, you can define in DMZ zone. This too have the feature of only selected incoming connections are accepted.
- Work Zone: In this zone, we can define only internal networks i.e. private networks traffic are allowed.
- Home Zone: This zone is specially used in home areas, we can use this zone to trust the other computers on networks to not harm your computer as every zone. This too allow only the selected incoming connections.
- Internal Zone: This one is similar to work zone with selected allowed connections.
- Trusted Zone: If we set the trusted zone all the traffic are accepted.
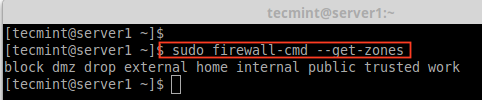
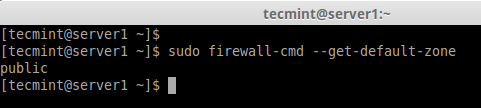
Now you’ve better idea about zones, now let’s find out available zones, default zones and list all zones using the following commands.
# firewall-cmd --get-zones
# firewall-cmd --get-default-zone
# firewall-cmd --list-all-zones
Note: The output of above command won’t fit into single page as this will list every zones like block, dmz, drop, external, home, internal, public, trusted, and work. If the zones have any rich-rules, enabled services or ports will be also listed with those respective zone informations.
Step 3: Setting Default Zone
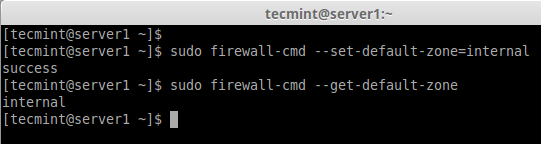
4. If you would like to set the default zone as internal, external, drop, work or any other zone, you can use the below command to set the default zone. Here we using “internal” zone as default.
# firewall-cmd --set-default-zone=internal
5. After setting zone, verify the default zone using below command.
# firewall-cmd --get-default-zone
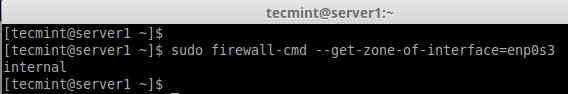
6. Here, our Interface is enp0s3, If we need to check our zone in which interface is bounded we can use the below command.
# firewall-cmd --get-zone-of-interface=enp0s3
7. Another interesting feature of firewalld is ‘icmptype‘ is the one of the icmp types supported by firewalld. To get the listing of supported icmp types we can use the below command.
# firewall-cmd --get-icmptypes
Step 4: Creating Own Services in Firewalld
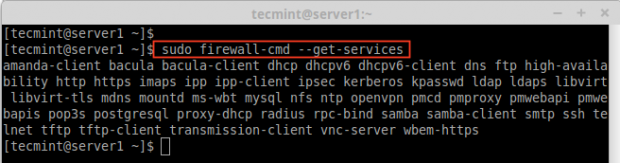
8. Services are set of rules with ports and options which is used by Firewalld. Services which are enabled, will be automatically loaded when the Firewalld service up and running. By default, many services are available, to get the list of all available services, use the following command.
# firewall-cmd --get-services
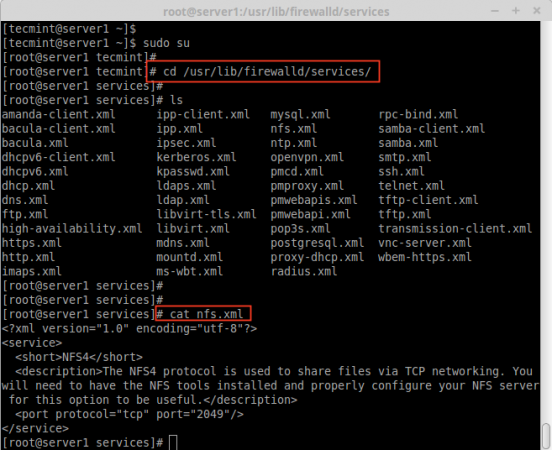
9. To get the list of all the default available services, go the the following directory, here you will get the list of services.
# cd /usr/lib/firewalld/services/
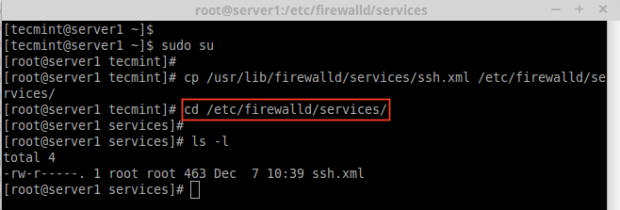
10. To create your own service, you need to define it at the following location. For example, here I want to add a service for RTMP port 1935, first make a copy of any one of the service from.
# cd /etc/firewalld/services/ # cp /usr/lib/firewalld/services/ssh.xml /etc/firewalld/services/
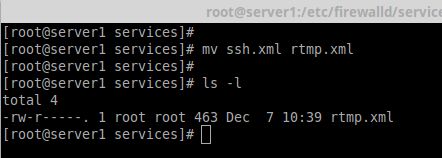
And then, navigate to the location were our service file was copied, next rename the file ‘ssh.xml‘ to ‘rtmp.xml‘ as shown in the below picture.
# cd /etc/firewalld/services/
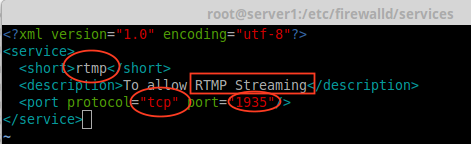
11. Next open and edit the file as Heading, Description, Protocol, and Port number, which we need to use for the RTMP service as shown in below picture.
12. To make these changes activate, restart the firewalld service or reload the settings.
# firewall-cmd --reload
13. To confirm, whether service is added or not, run below command to get list of services available.
# firewall-cmd --get-services
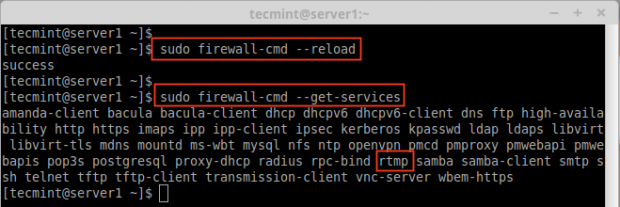
Confirm Added Service in Firewall
Step 5: Assigning Services to Zones
14. Here we are going to see how to manage the firewall using ‘firewall-cmd‘ command. To know the current state of the firewall and all active zones, type the following command.
# firewall-cmd --state # firewall-cmd --get-active-zones
15. To get the public zone for interface enp0s3, this is the default interface, which is defined in /etc/firewalld/firewalld.conf file as DefaultZone=public.
To list all available services in this default interface zone.
# firewall-cmd --get-service
Step 6: Adding Services to Zones
16. In the above examples, we have seen how to create own services by creating rtmp service, here we will see how to add the rtmp service to the zone as well.
# firewall-cmd --add-service=rtmp
17. To remove added zone, type.
# firewall-cmd --zone=public --remove-service=rtmp
The above step was temporary period only. To make it permanent we need to run the below command with option –permanent.
# firewall-cmd --add-service=rtmp --permanent # firewall-cmd --reload
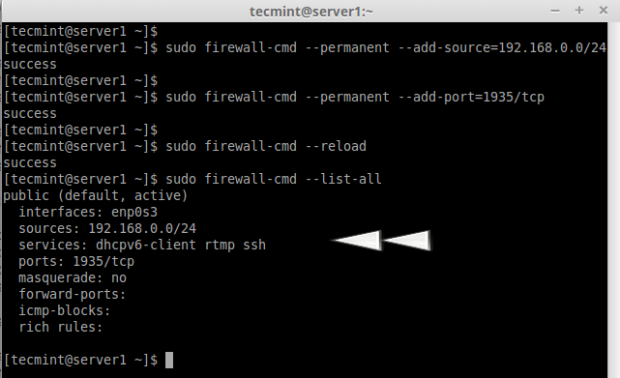
18. Define rules for network source range and open anyone of the port. For example, if you would like to open a network range say ‘192.168.0.0/24’ and port ‘1935’ use the following commands.
# firewall-cmd --permanent --add-source=192.168.0.0/24 # firewall-cmd --permanent --add-port=1935/tcp
Make sure to reload firewalld service after adding or removing any services or ports.
# firewall-cmd --reload # firewall-cmd --list-all
Step 7: Adding Rich Rules for Network Range
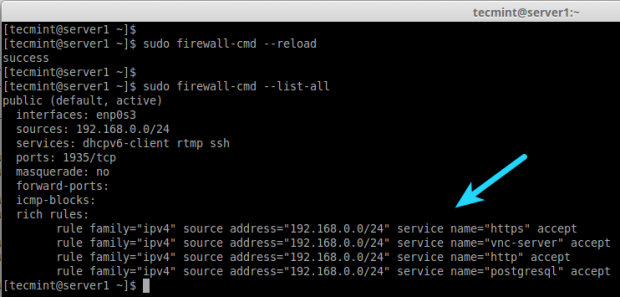
19. If I want to allow the services such as http, https, vnc-server, PostgreSQL, you use the following rules. First add the rule and make it permanent and reload the rules and check the status.
# firewall-cmd --add-rich-rule 'rule family="ipv4" source address="192.168.0.0/24" service name="http" accept' # firewall-cmd --add-rich-rule 'rule family="ipv4" source address="192.168.0.0/24" service name="http" accept' --permanent # firewall-cmd --add-rich-rule 'rule family="ipv4" source address="192.168.0.0/24" service name="https" accept' # firewall-cmd --add-rich-rule 'rule family="ipv4" source address="192.168.0.0/24" service name="https" accept' --permanent # firewall-cmd --add-rich-rule 'rule family="ipv4" source address="192.168.0.0/24" service name="vnc-server" accept' # firewall-cmd --add-rich-rule 'rule family="ipv4" source address="192.168.0.0/24" service name="vnc-server" accept' --permanent # firewall-cmd --add-rich-rule 'rule family="ipv4" source address="192.168.0.0/24" service name="postgresql" accept' # firewall-cmd --add-rich-rule 'rule family="ipv4" source address="192.168.0.0/24" service name="postgresql" accept' --permanent
Now, the Network range 192.168.0.0/24 can use the above service from my server. The option –permanent can be used in every rule, but we have to define the rule and check with the client access after that we have to make it permanent.
20. After adding above rules, don’t forget to reload the firewall rules and list the rules using:
# firewall-cmd --reload # firewall-cmd --list-all
To know more about Firewalld.
# man firewalld
That’s it, we have seen how to setup net-filter using Firewalld in RHEL/CentOS 7 and Fedora 21.
Conclusion
Net-filter is the framework for firewall for each and every Linux distributions. Back in every RHEL and CentOS editions we used iptables but in version 7 they have introduced Firewalld. It’s easier to understand and use firewalld. Hope you have enjoyed the write-up.